Azure Sentinel

Mobile alerting with tracking & escalation for Azure Sentinel
![]() Why Enterprise Alert
Why Enterprise Alert
Azure Sentinel is a cloud native SIEM solution from Microsoft and a security alert provider in Azure Graph Security API. However, the level of alert details available with the Graph Security API is limited for Azure Sentinel. The connector can therefore augment alerts with further details (insights rule search results), from the underlying Azure Sentinel Log Analytics workspace. To be able to do that, the connector communicates with Azure Log Analytics REST API and needs according permissions (see below). Furthermore, the app can also update the status of Azure Sentinel incidents, when all related security alerts are e.g. in progress or resolved. In order to be able to do that, the connector needs to be a member of the ‘Azure Sentinel Contributors’ group in your Azure Subscription.
Once added to your Enterprise Alert tenant, the connector will read security alerts from Azure Graph Security API and fully automatically and trigger alert notifications to your team members on duty. It will also synchronize the alert status from Enterprise Alert to Graph Security API, so that if alerts are acknowledged or closed, this status is also updated on the according Azure Graph Security API alert or the corresponding security provider. As mentioned, the connector mainly uses Azure Graph Security API, but for some security providers, such as Azure Sentinel, it also uses dedicated REST APIs from according Azure solutions.
![]() How it works
How it works
The connector for Azure Sentinel, Azure Security Center and other Azure Graph Security API providers provides seamless 2-way integration with your Azure Security solutions.
![]() Integration capabilities
Integration capabilities
- Staff can acknowledge and take ownership for critical events that occur
- Communicate within an alert to address a particular problem
- Alerts are escalated in case of no response
- On-call scheduling to alert the right people at the right time
![]() Scenarios
Scenarios
- Application Management
- Operational Data Alerts
- Real-time System Insights
HOW TO INTEGRATE
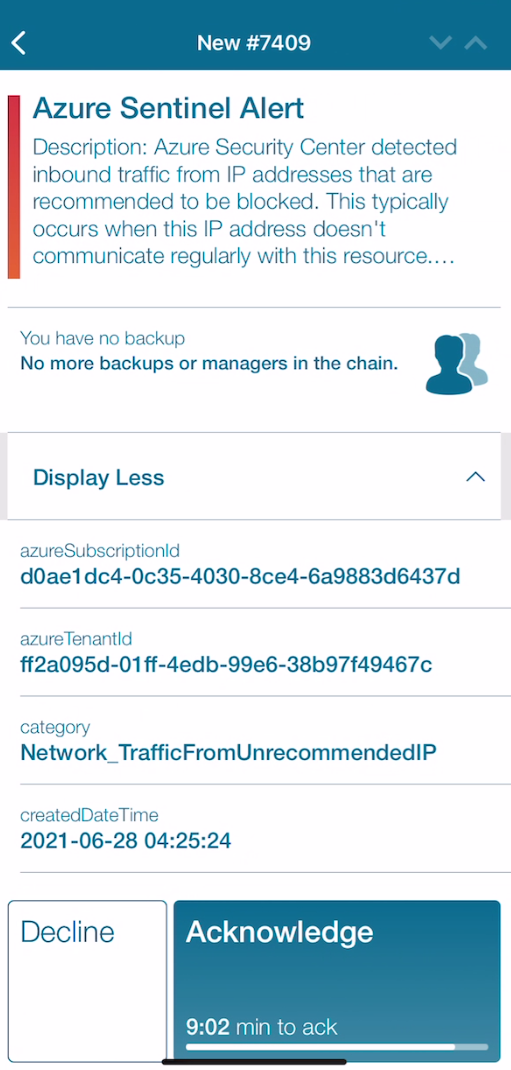
In our example we will use Azure Sentinel to generate an alarm. The smart connector from EA will receive this as an incoming event and raise an alert based on policy conditions.
Integration Steps
First we need to setup the connector within Enterprise Alert. Navigate to System > Event Sources and click on New Source at the bottom of the portal. This launches the gallery and select Azure Sentinel.
1. Download the PowerShell deployment script from here.
2. Review the script and the roles and permission scopes it deploys for the new app registration. If you don’t want to use the connector with Azure Sentinel, you could remove all role creation and role assignment code and only use it to create the app registration (SPN) in your Azure Active Directory.
3. Run the script. At the end it outputs information that you need to enter in the connector app configuration.
4. In Azure AD, click on ‘App Registrations’. Find the app with the name ‘SIGNL4AzureSecurity’ and open its details
5. On the left menu blade click ‘API Permissions’. Then click ‘Add a permission’.
6. On the blade that loads, under ‘Microsoft APIs’ click on the ‘Microsoft Graph’ tile, then click ‘App permission’.
7. In the table that is displayed expand ‘SecurityEvents’ and check ‘SecurityEvents.Read.All’ and ‘SecurityEvents.ReadWrite.All’.
8. Click ‘Add permissions’.
Configuring this app
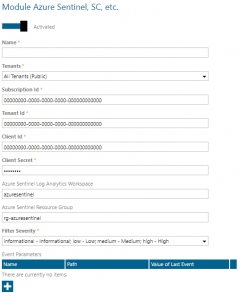
Finally, enter the IDs, that the script has outputted in the connector configuration:
- Azure Tenant ID
- Azure Subscription ID
- Client ID (of the enterprise application)
- Client Secret (of the enterprise application)
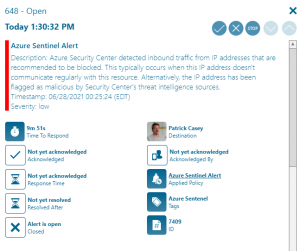
That’s it! Once the policy triggers, alerts will be visible via the web portal as well as the mobile app.