Enterprise Alert is the premier solution for reliable, targeted, and accountable Alerting. At Derdack, we have always aimed to provide the best possible security combined with an easy to use User interface. Part of this UI is the Enterprise Alert mobile App which supports secure 2-factor authentication by integrating with ADFS. With the current trend of moving more critical infrastructure into the cloud, while at the same time still utilizing on-premise products like Active Directory, you are often faced with Hybrid scenarios were users still live in AD while you want to utilize new Features like Azure Active Directory (AAD) as your primary identity provider. We stepped up to the challenge and enhanced our authentication capabilities to support secure mobile Authentication with AAD in such scenarios.
Following the steps below allows the Enterprise Alert Mobile App to connect to Enterprise Alert’s own Identity server which will offer you a normal login but also provide the option to authenticate through AAD. The AAD login will forward you to a Microsoft login page allowing you to log in like you are used to, with or without 2-factor authentications, based on your global and user-specific settings. Once you have successfully logged in, we will receive a claim containing your UPN allowing us to match your login against the users Synced in via AD.
To get this going you will need administrative access to your Azure Active Directory to register a new Application as well as administrative access to the Enterprise Alert Server to edit the necessary config files. Let’s dive into the detailed Steps now:
- Log in to the admin console of your Azure Active Directory and navigate to App registrations and click on +New registration
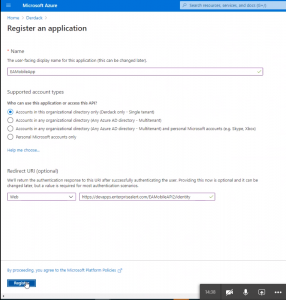
- Give that App a name and provide a Redirect URI in the format HTTPS://<your_server>/EAMobileAPI/identity (this string has to be 100% case sensitive match) once you are done click on register
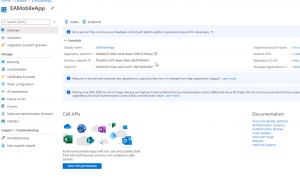
- Note down the Application (client) ID as well as the Directory (tenant) ID
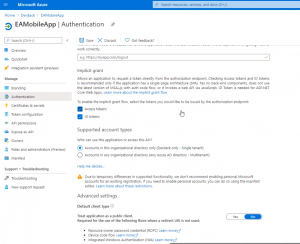
- On the left side menu, click on Authentication and activate the implicit grant flow by checking the boxes for Access Tokens and ID tokens, afterwards hit save at the top.
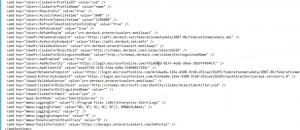
- Open the web.config file under …/Enterprise Alert/websites/EAMobileAPI/ and set the values for AadAuthority (=Directory (tenant) ID) and for AadClientId (=Application (client) ID) also make sure to activate AAD authentication by setting the value for AadEnabled to true. Once done save the change and restart the IIS.
This should be everything that needs to be done to get secure mobile Authentication with AAD going. When you connect your app to Enterprise Alert the next time you will have the option to select AAD as an authentication method.
